Comet-Hosted Management Console configuration
Overview
The Comet-Hosted Management Console settings can be configured via your:
- Comet Account Portal
- Comet-Hosted Management Console
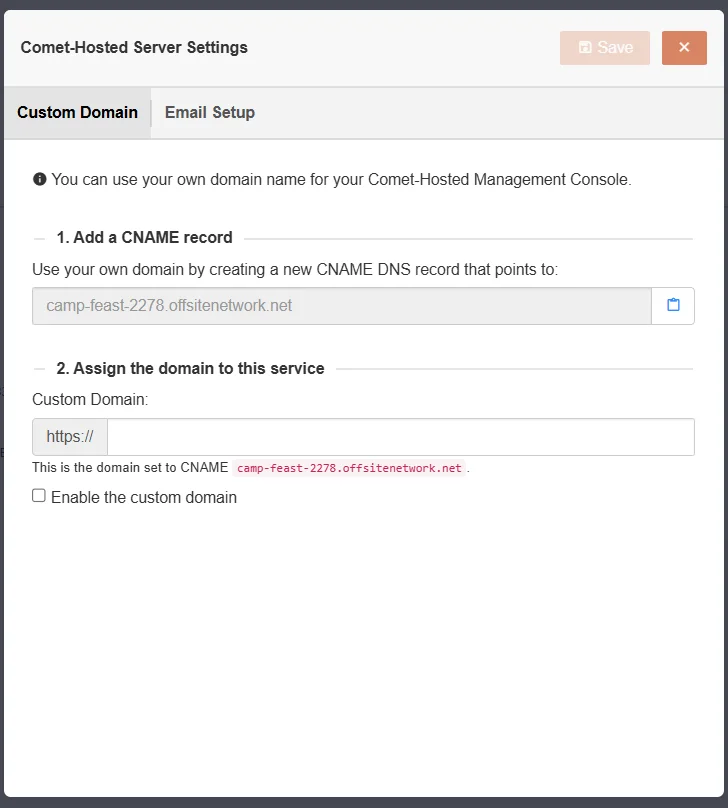
Configure a custom domain
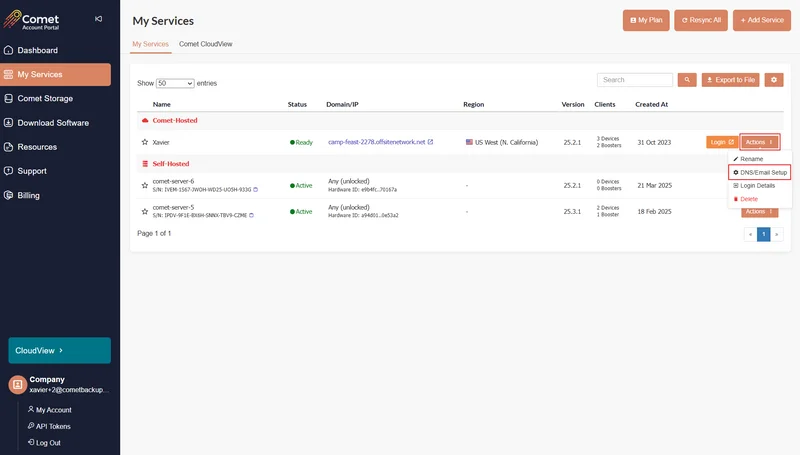
In the "My Services" section of your Comet Account Portal, select "Actions" on the right, then select "DNS/Email Setup".
Email reporting
Configure email reporting sending option
Configure your email sending options. These are used for sending reports to end users or admins.
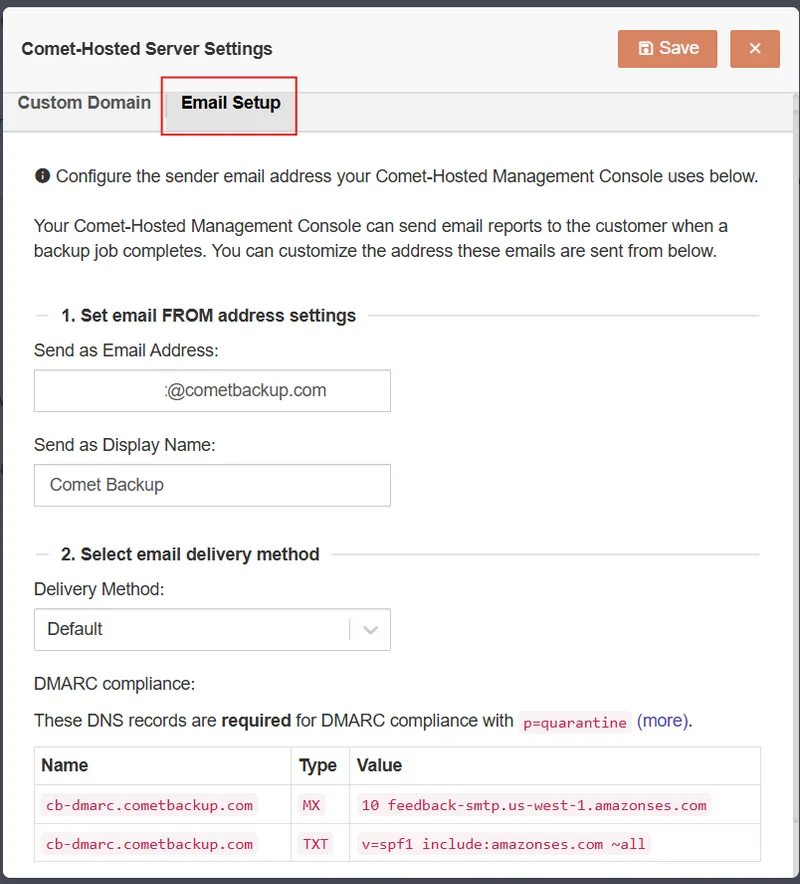
Delivery Method: Default
The default email delivery method uses AWS SES to send emails on behalf of a verified email. During the creation of your Comet-Hosted Server you will recieve an Email Address Verification email from noreply@cometbackup.com. Click the link in this email to verify your send-as account.
To configure DMARC compliance when sending email reports from a Comet-Hosted Server you need to configure a couple DNS record on the top-level of your domain. This is recommended to prevent reports going to spam.
| Name | Type | Value |
|---|---|---|
cb-dmarc.<domain> | MX | 10 feedback-smtp.us-west-1.amazonses.com |
cb-dmarc.<domain> | TXT | v=spf1 include:amazonses.com ~all |
To confirm that these values are correct, click the 'Validate DNS Records' button. Note: Some providers may take up to 72 hours to propagate these changes.
Delivery Method: Custom SMTP Server
Use this option if you want to send emails using an Office 365 or Google SMTP relay.
If the default email deliver method does not suit your needs, it is possible to confirm email reports to be sent using a custom SMTP server. Switch the 'Delivery Method' option to 'Custom SMTP Server', and enter the authentication details for your custom SMTP server/relay. You can test that the server can connect to this server by clicking the 'Test SMTP Credentials' button.
Configure email reports
Refer to our guide on managing backups efficiently with email reporting for more information on setting up email reports.
Storage Template
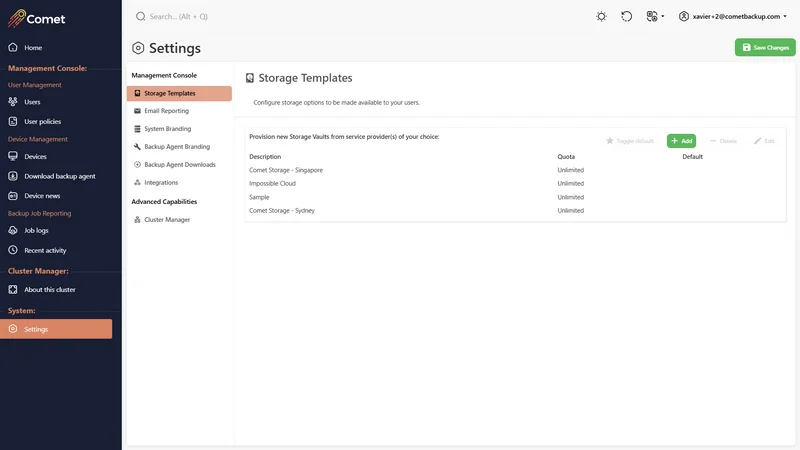
The Storage Template will automatically assign a bucket location within the storage location. It is possible to configure it with your Self-Hosted Storage Gateway location/s and to a cloud storage provider directly.
Configure a Storage Template to backup directly to a cloud provider
You can configure a Storage Template with one of the supported cloud storage providers. When using this Storage Vault, the data will backup directly to the storage location and not pass through your Self-Hosted Storage Gateway (unlike using your cloud storage as the storage destination for Storage Gateway). When assigning this Storage Vault to an account, the access keys granted will only have permissions for its own subdirectory and won't be able to access other accounts data.
Create a new Storage Vault, change the Type dropdown to one of the supported cloud providers, and input your cloud storage details (Master key is required).
Current supported providers for direct-to-cloud Storage Template
- Amazon AWS
- Backblaze B2 Cloud Storage
- Comet Storage powered by Wasabi
- IDrive e2
- Impossible Cloud
- Storj DCS
- Wasabi Hot Cloud Storage
- Custom IAM-Compatible
Video tutorial
See our video on how to configure direct-to-cloud storage with Comet:
System branding
You can configure the appearance of the Comet Management Console web interface.
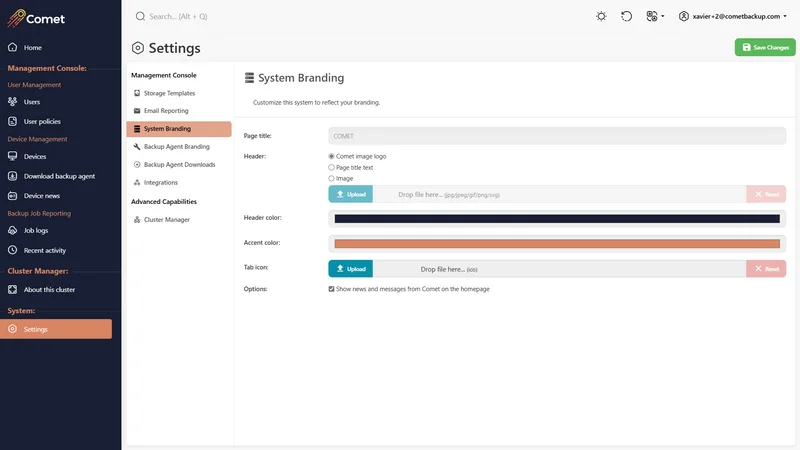
For more information on re-branding the Comet Management Console, please refer to our re-branding guide.
Backup agent branding
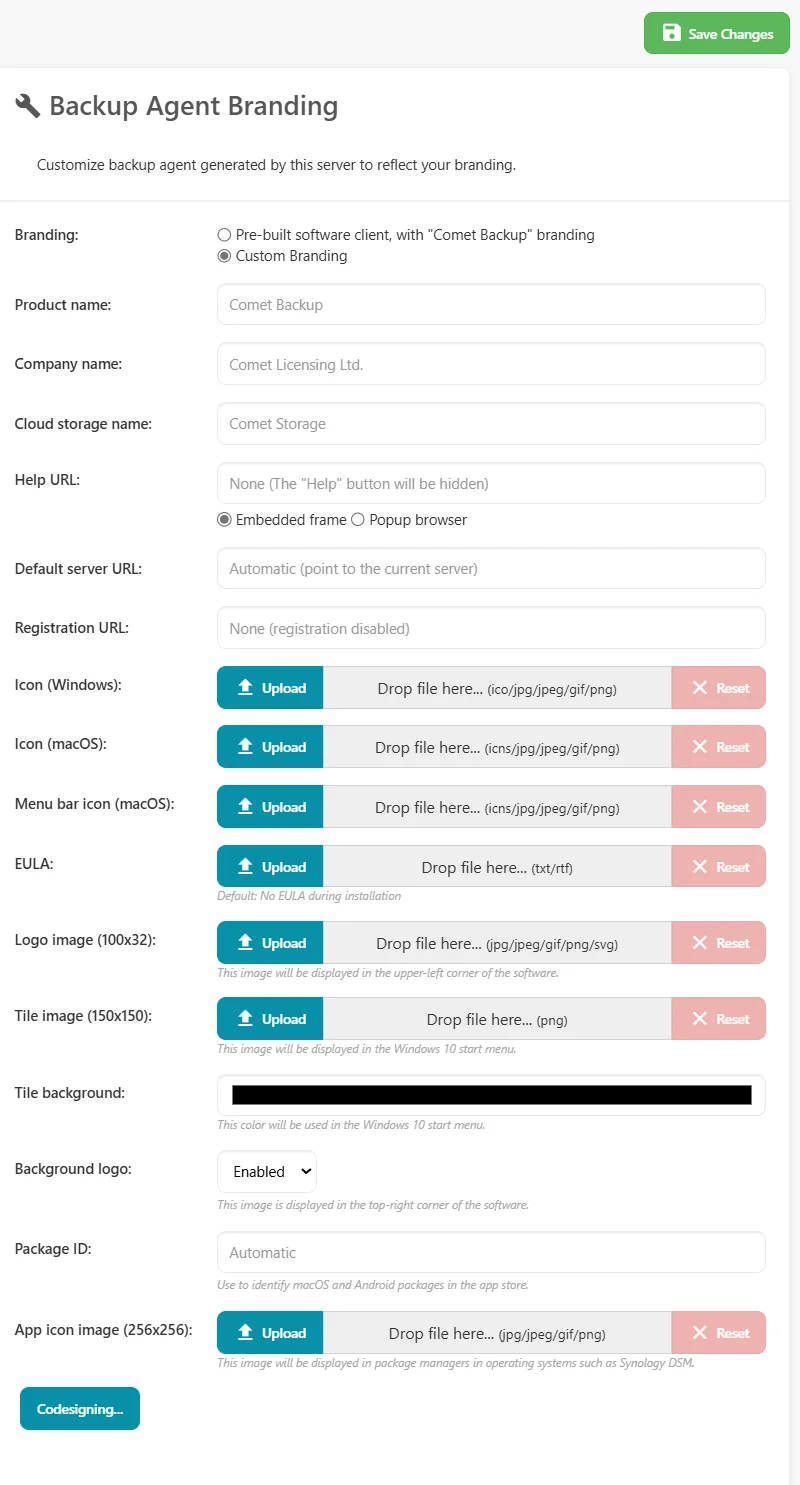
The Backup Agent Branding section is for rebranding the Comet desktop client. This can also be configured within cometd.cfg. When you make changes to your branding, it is required to update the desktop clients for the changes to apply. It is possible to update the branding for multiple devices at once using the Bulk device upgrade feature).
For more information, please refer to our full guide on re-branding the Comet Backup Client and details on codesigning the Comet Backup Client.
There is also a separate guide on re-branding the Comet interface.
Backup agent downloads
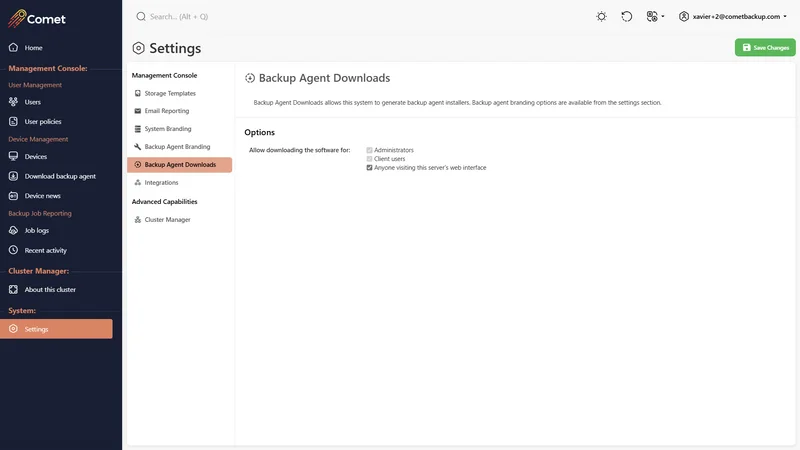
The Backup Agent Downloads is the part of Comet Management Console responsible for generating branded client software installers.
Options
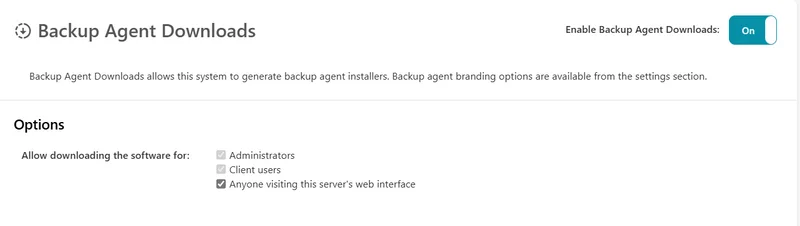
Video tutorial
Integrations
Comet integrates with a handful of third party services. Check out the Third-party Service Addons for more details.