Protected Item types
Overview
Comet supports a range of different types for your Protected Item configuration, including file, application, system, and VM backup types.
Protected Items are private to each device. To move or duplicate Protected Item configurations from one device to another, see here: https://docs.cometbackup.com/latest/installation/comet-server-usage#copy-and-paste
Protected Items can be configured on the Comet Management Console as well as on the Comet Backup client. In the Comet Management Console, Protected Items are configured on the User Profile under the Protected Items tab per device.
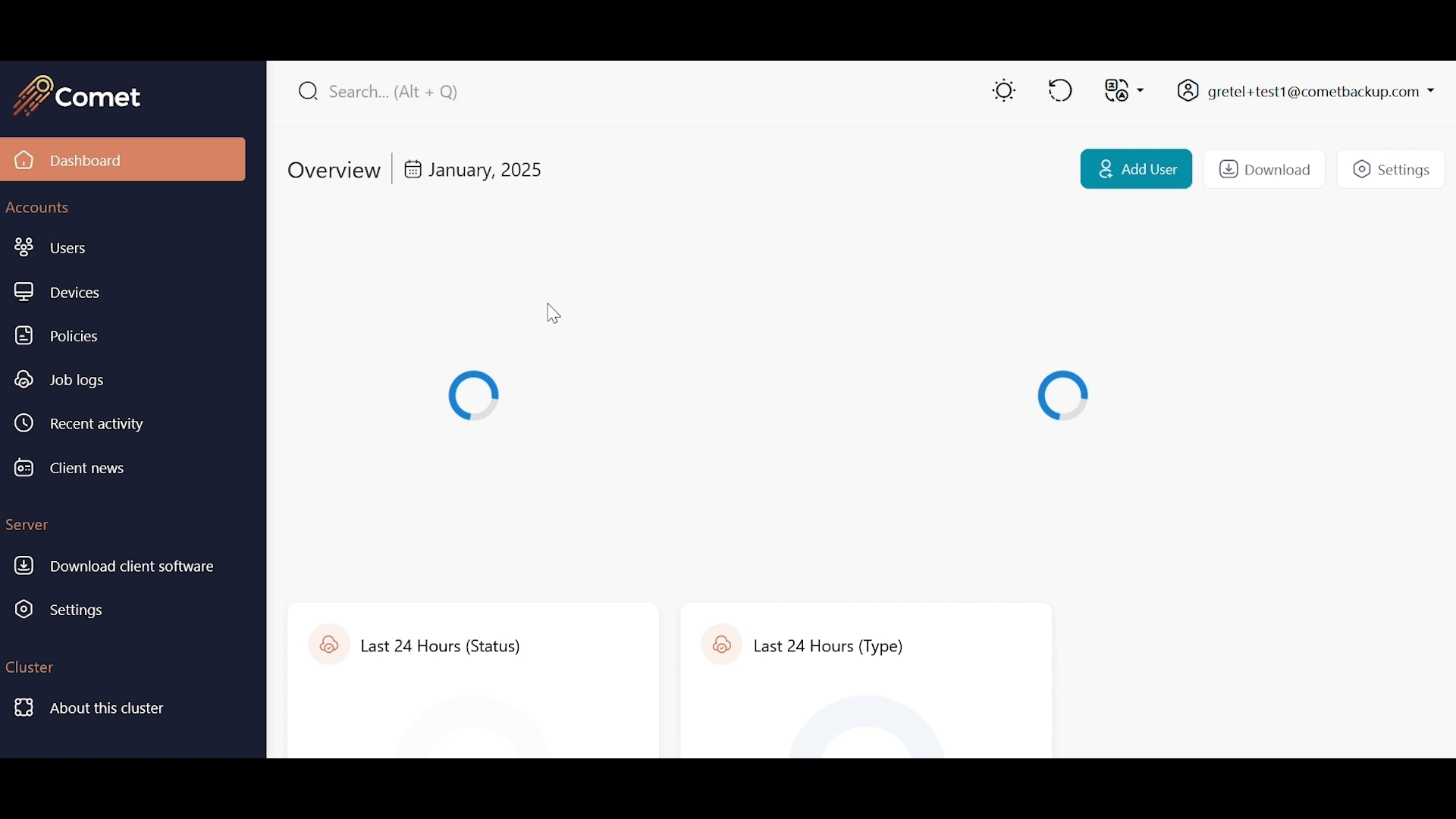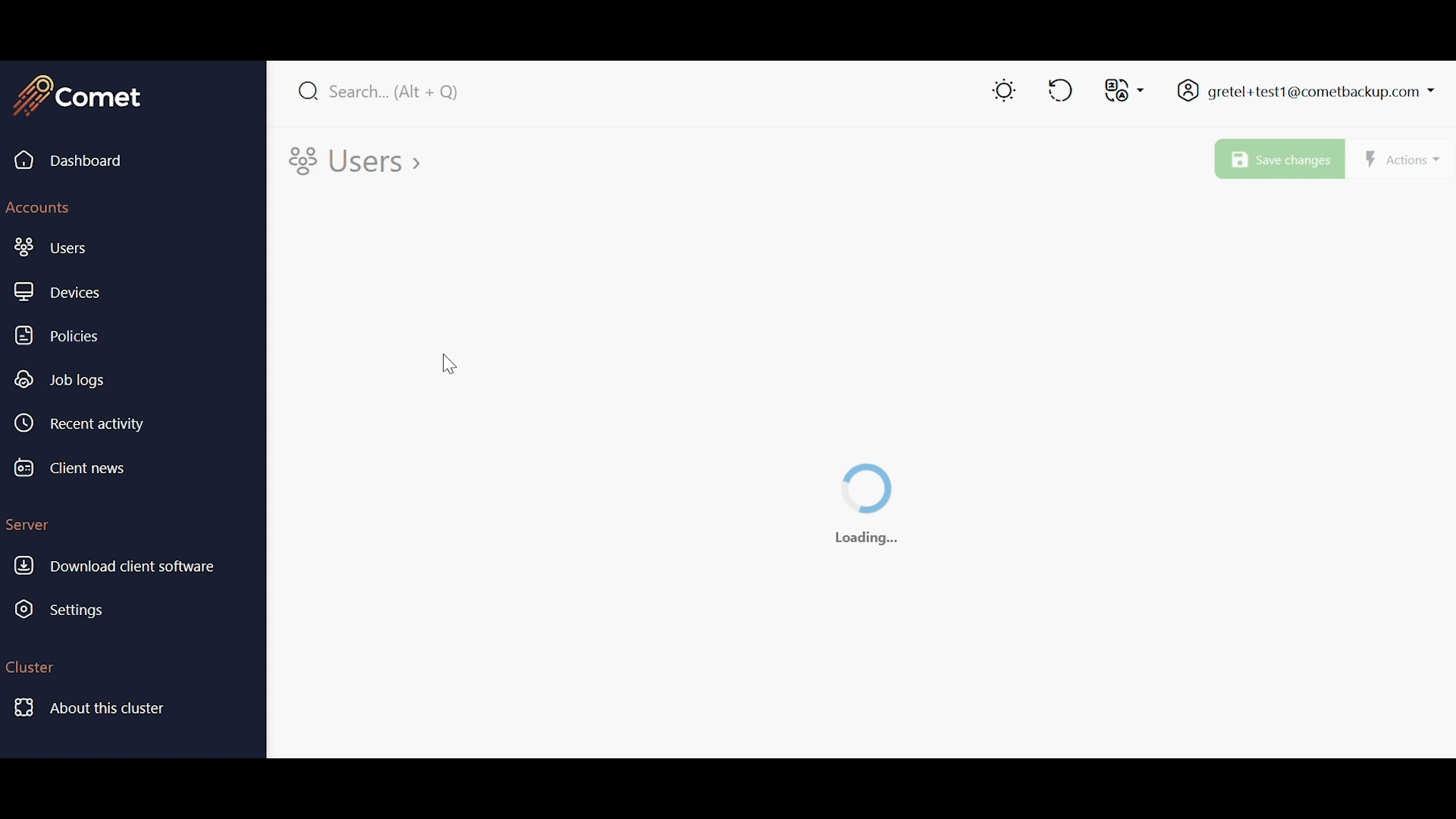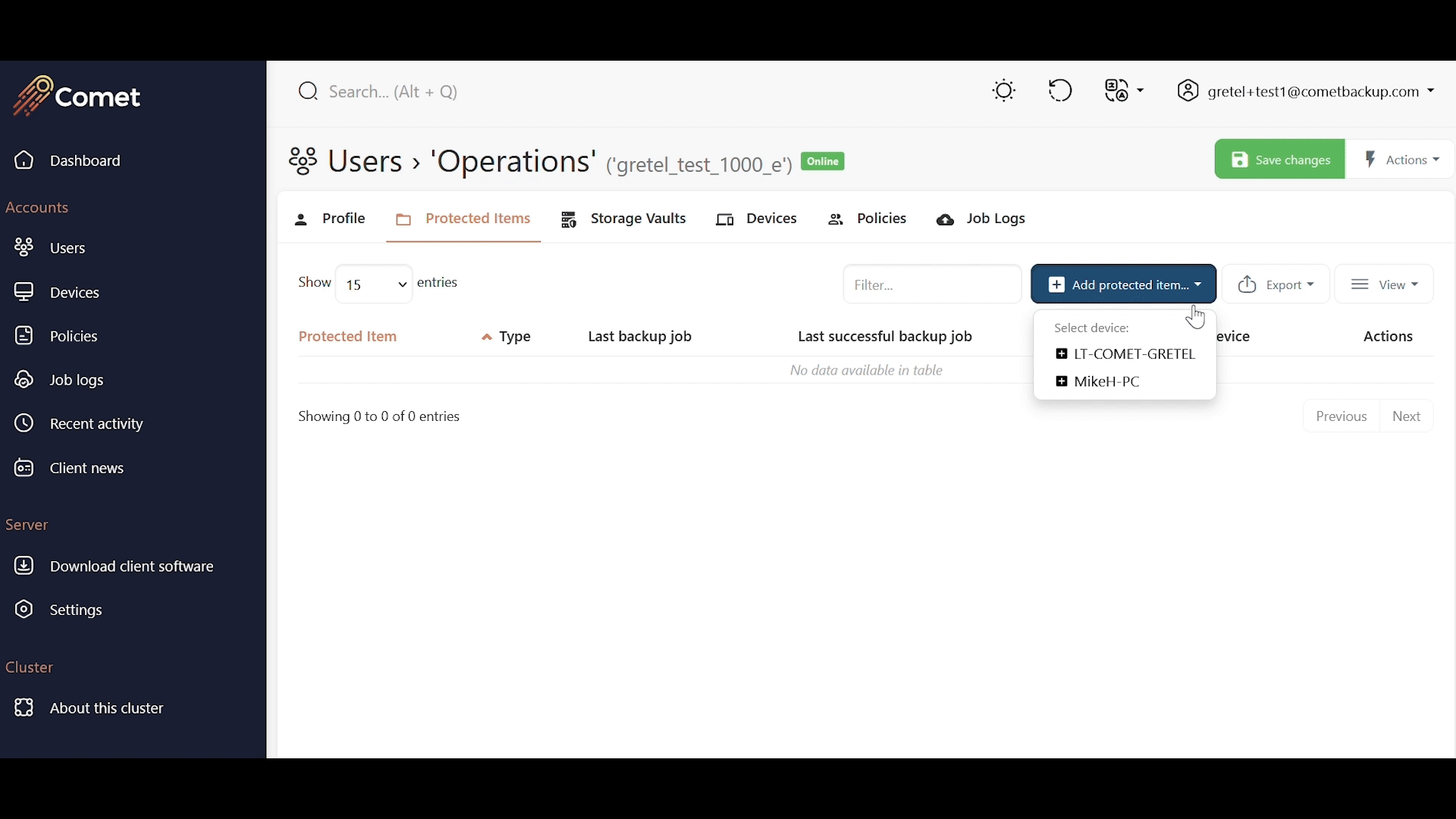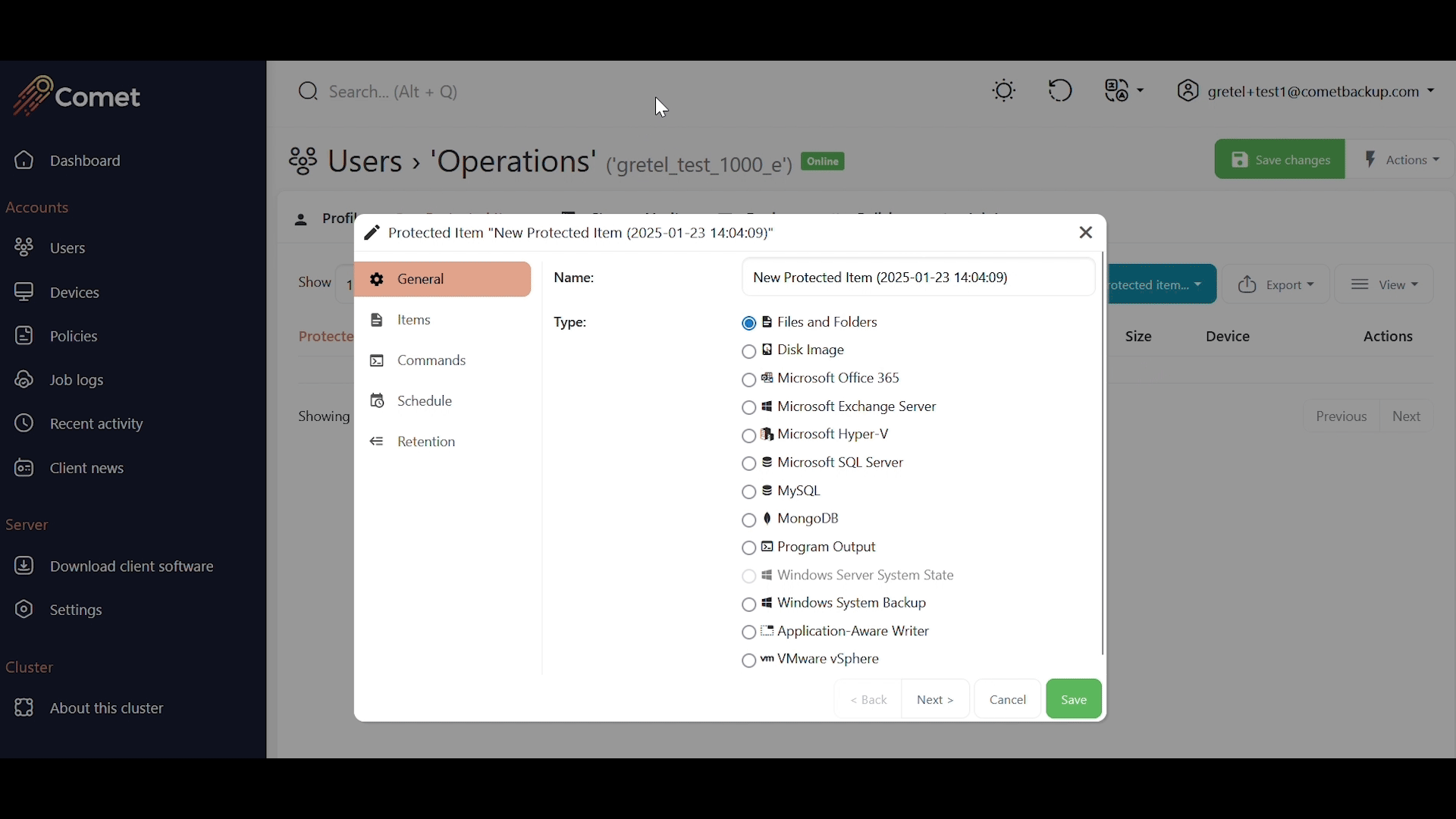
Protected Items can also be configured on the Comet Backup Client, as long as they are not restricted by policy settings.
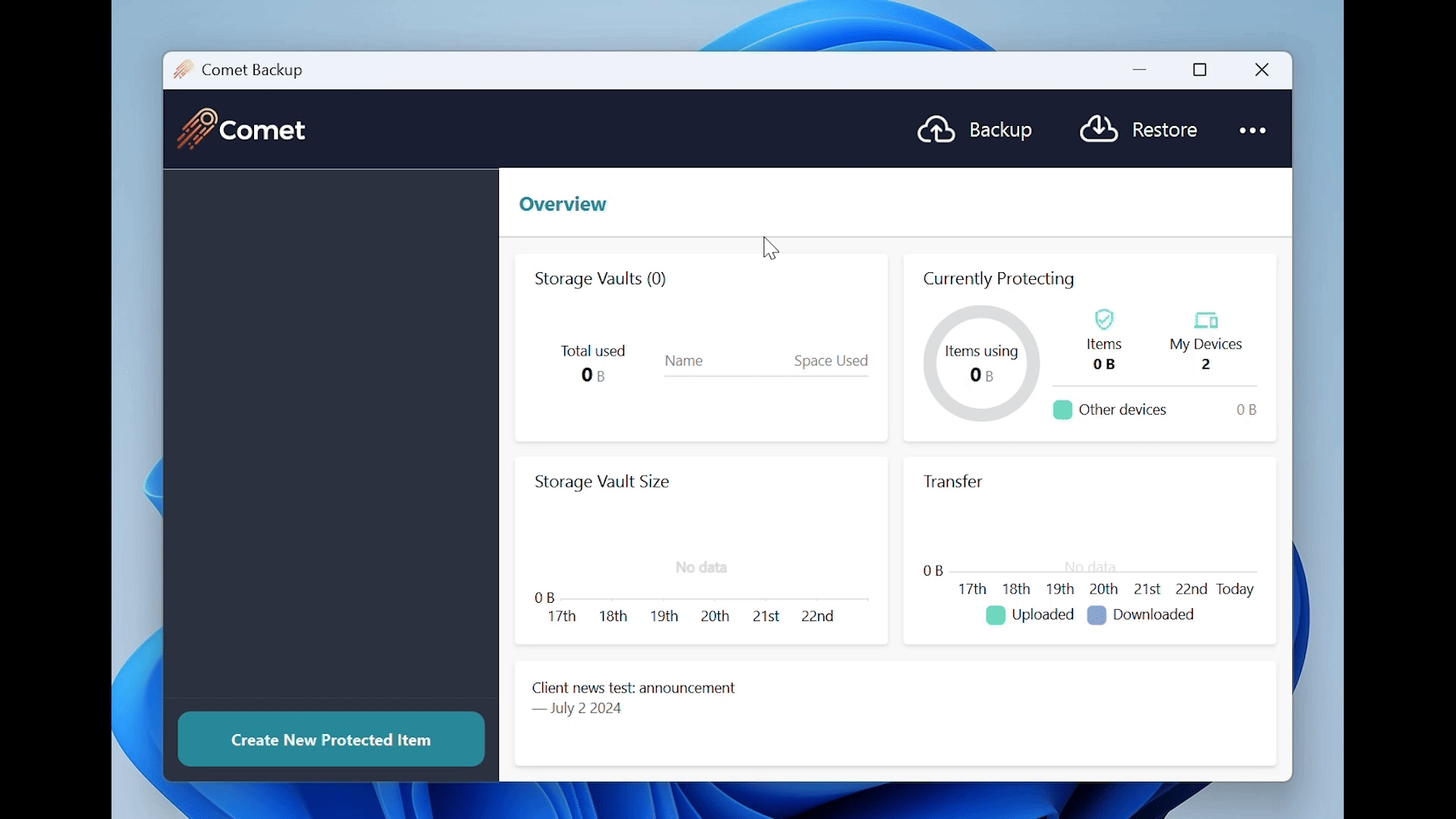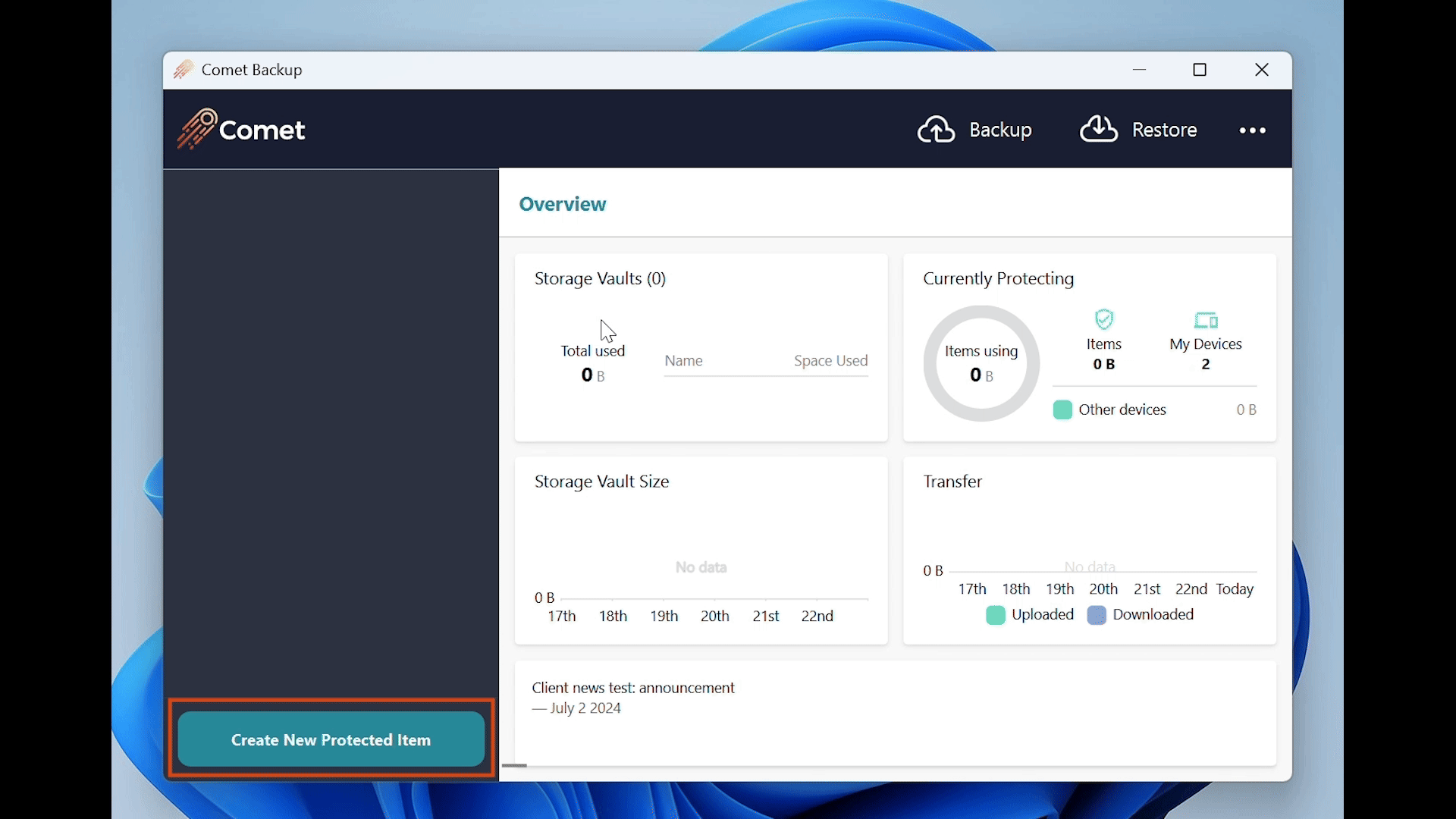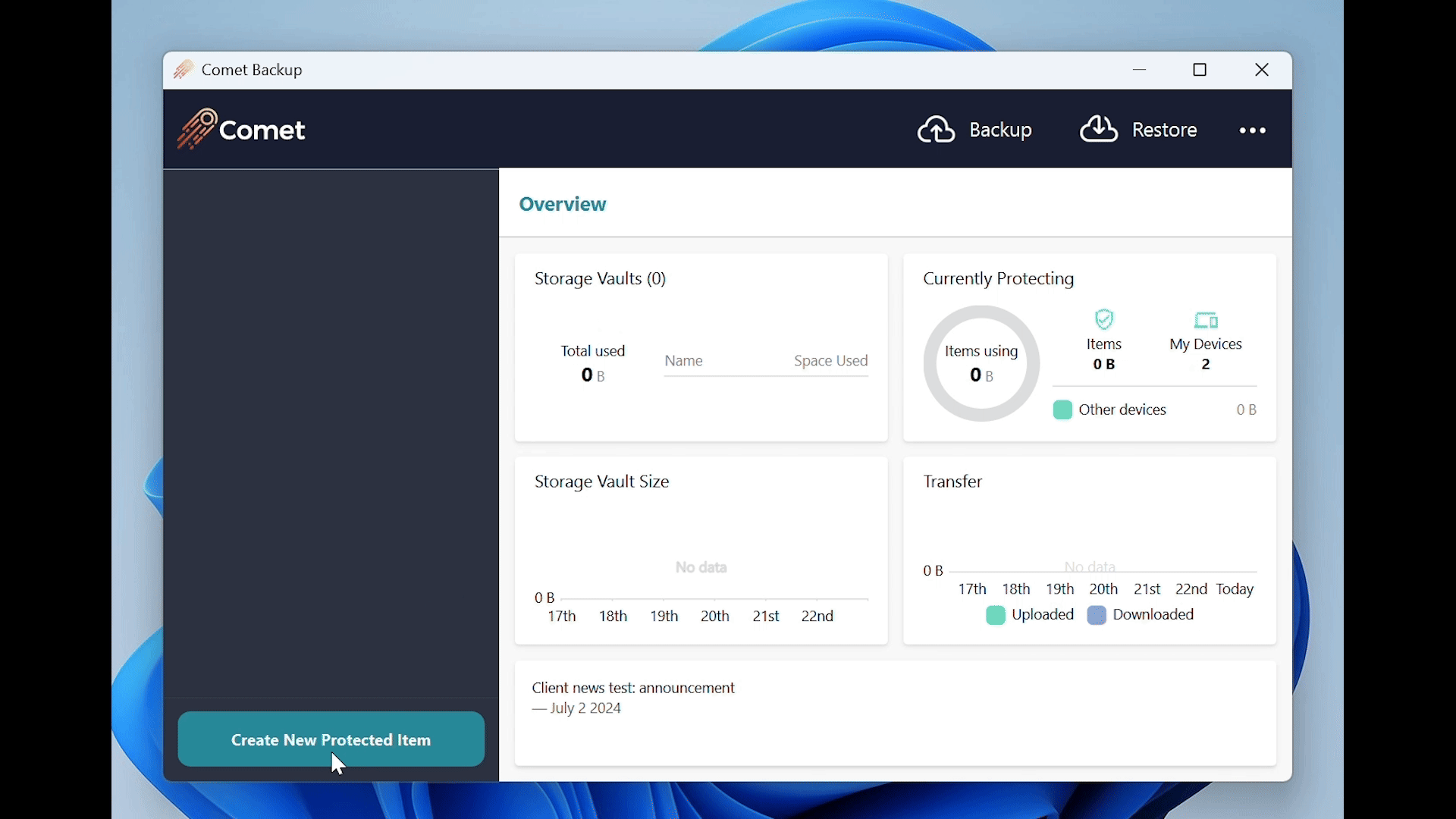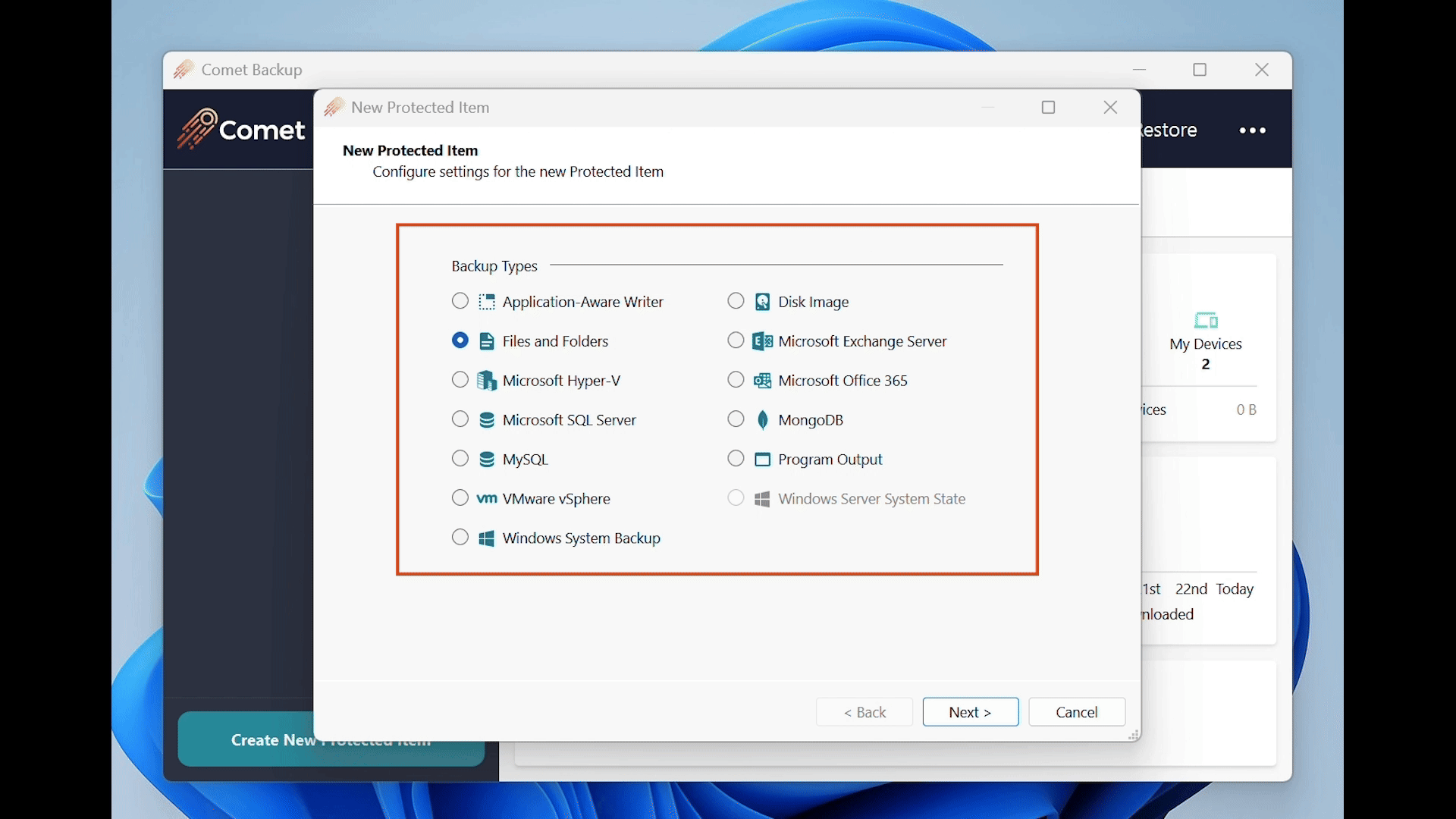
The following guides specify the backup and restore steps specific to each Protected Item and provides details on the underlying technology for each.